Скачать с ютуб The DevSecOps Playbook: A step-by-step guide to implementing DevSecOps .. - Paul McCarty в хорошем качестве
Скачать бесплатно The DevSecOps Playbook: A step-by-step guide to implementing DevSecOps .. - Paul McCarty в качестве 4к (2к / 1080p)
У нас вы можете посмотреть бесплатно The DevSecOps Playbook: A step-by-step guide to implementing DevSecOps .. - Paul McCarty или скачать в максимальном доступном качестве, которое было загружено на ютуб. Для скачивания выберите вариант из формы ниже:
Загрузить музыку / рингтон The DevSecOps Playbook: A step-by-step guide to implementing DevSecOps .. - Paul McCarty в формате MP3:
Если кнопки скачивания не
загрузились
НАЖМИТЕ ЗДЕСЬ или обновите страницу
Если возникают проблемы со скачиванием, пожалуйста напишите в поддержку по адресу внизу
страницы.
Спасибо за использование сервиса savevideohd.ru
The DevSecOps Playbook: A step-by-step guide to implementing DevSecOps .. - Paul McCarty
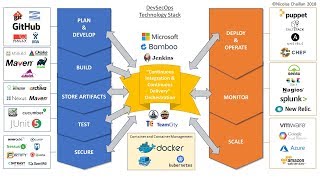
What is DevSecOps? How do I "do" it? There's a lot of hype around DevSecOps right now, and getting two people to agree on exactly what it means can be a challenge. Unfortunately, there's a lot of vendor narrative that says it's CI/CD with some security thrown in for good measure, but DevSecOps is a lot more than that! My career was changed by the DevOps movement and I believe that DevSecOps should be built on top of DevOps. What does that mean? Well, what made DevOps so powerful for me in the late 2000's was that it brought together people from different departments to work together. Developers learned more about how to manage the underlying infrastructure, and ops teams learned how to use code to build and manage automation. This was powerful and I believe we can do the same with DevSecOps: bring security teams into the processes and workflows that DevOps built at at the same time those security teams will evolve to understand how operations and development teams work. This talk will cover my DevSecOps Playbook which is an open source step-by-step guide to implementing DevSecOps for any organization. This Playbook is broken down into 5 distinct areas of domain expertise: 1. Development Environment 2. Source Code Management 3. Continuous Integration / Deployment and other Automation 4. Deployment Environments 5. Organization The DevSecOps Playbooks spreads the controls evenly across these 5 domains and highlights that this is a group responsibility. There is also an addendum for compliance frameworks and how they can map to the tasks and controls listed in the Playbook. In this talk I will outline these 5 areas and talk about the different controls and tasks in each. I will also give examples of how to implement each of the functions. Each task has a priority and a difficulty. The priority is a number one to three with one being the most important set of tasks to do, and three being the last set of tasks you should do. So for example, Difficulty defines how hard a particular step is. So for example, using a credential store instead of .env files is a priority one, but a difficulty two. This shows that the task should be prioritized, but at the same time shows that there it is not a trivial thing to do. At the end of this talk, my listeners should come away with many specific security tasks that they can use in their own SDLC processes, and will have seen concrete examples of how each task can implemented. Presenter: Paul McCarty, SecureStack, Founder (Apiiro Room, Day 1, Session 1)