Скачать с ютуб CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi в хорошем качестве
Из-за периодической блокировки нашего сайта РКН сервисами, просим воспользоваться резервным адресом:
Загрузить через ClipSave.ruСкачать бесплатно CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi в качестве 4к (2к / 1080p)
У нас вы можете посмотреть бесплатно CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi или скачать в максимальном доступном качестве, которое было загружено на ютуб. Для скачивания выберите вариант из формы ниже:
Загрузить музыку / рингтон CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi в формате MP3:
Если кнопки скачивания не
загрузились
НАЖМИТЕ ЗДЕСЬ или обновите страницу
Если возникают проблемы со скачиванием, пожалуйста напишите в поддержку по адресу внизу
страницы.
Спасибо за использование сервиса savevideohd.ru
CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi
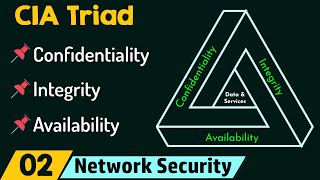
Welcome to another exciting episode from Cyberwings Security! The CIA Model, also known as the CIA Triad, is a foundational model for information security. It stands for Confidentiality, Integrity, and Availability, and it represents the three core security properties that must be protected in order to ensure the safety and security of information systems. Confidentiality means that information is only accessible to those who are authorized to access it. This includes protecting data at rest, in transit, and in use. Integrity means that information is accurate and complete, and that it has not been tampered with or altered in any way. Availability means that information is accessible to authorized users when they need it. This includes protecting systems from denial-of-service attacks and other disruptions. Authenticity means that information is genuine and can be trusted. This includes protecting systems from spoofing and other attacks that can be used to create counterfeit or misleading information. Non-repudiation means that it is not possible for a user to deny performing an action that they have actually performed. This is important for ensuring accountability and preventing fraud. The CIA Model is widely used by organizations of all sizes to develop and implement security policies and procedures. It is also used by security professionals to assess the security risks of information systems and to design and implement security solutions. In this video, we will discuss the CIA Model in more detail and explain how it can be used to improve the security of your information systems. Topics covered in this video: What is the CIA Model? Why is the CIA Model important? How to protect confidentiality, integrity, and availability How to ensure authenticity and non-repudiation Real-world examples of CIA Model attacks and defenses Watch this video to learn more about the CIA Model and how to use it to protect your information systems. Connect with me: 📷 Instagram: / rahulkumar_2620 💼 LinkedIn: / rahul-kumar-b35794165 📟 Join me on WhatsApp: https://whatsapp.com/channel/0029VaDX... 🌐 Website: https://cws.net.in/ 📡 Telegram Channel: - https://t.me/Channel_CWS 👍 If you find this video helpful, don't forget to give it a thumbs up and share it with your network. Subscribe to our channel for more insightful content on ethical hacking, digital forensics, and penetration testing. 🔔 Hit the notification bell to stay updated whenever we release new videos! Have questions or ideas for future topics? Drop them in the comments below. #cybersecurity #ethicalhacking #digitalforensics #penetrationtesting #CyberwingsSecurity #InfoSec #OnlineSafety #DataProtection #CyberAwareness #CybersecurityExplained #TechTips #LearnCybersecurity #HackerSkills #CyberEducation #CyberTech #SecurityTools #CyberLearning #ITSecurity #CyberThreats #cybersecuritycareers #cybersecuritytips #cybersecurityforbeginners